1. Introduction
Effectively intercept 99.9% of illegal modification of web pages, tampering of files, etc. Note: Cannot be used with other anti-tamper software
Note: Cannot be used with Website Tamper-proof.
2. Function list and detailed explanation
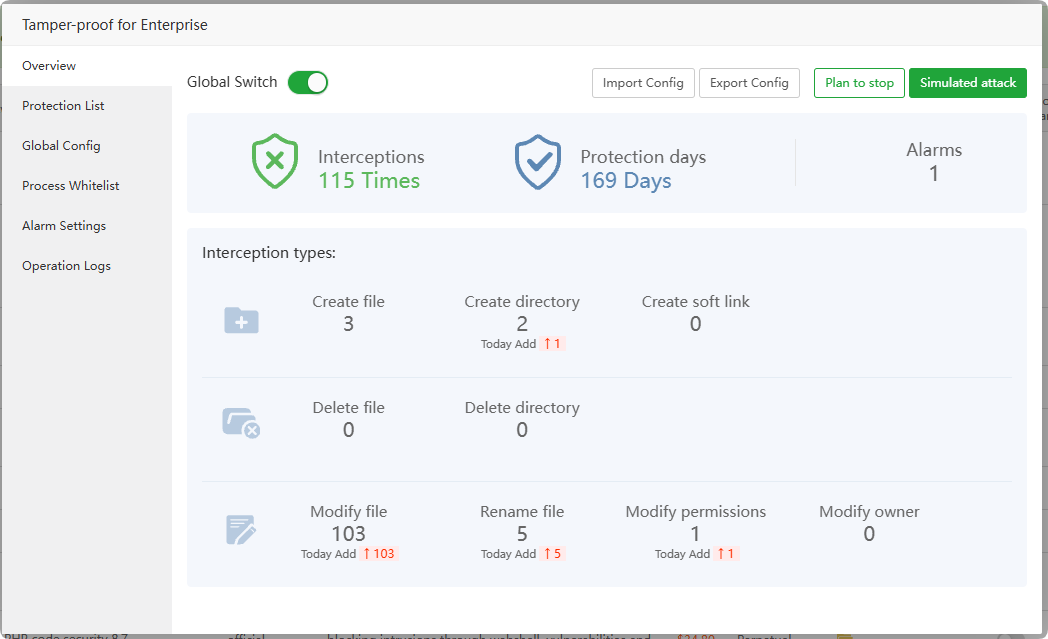
Overview
View the protection status of Tamper-proof for Enterprise
Global switch, if closed, all protected list directories will lose protection
Simulated attack can simulate whether the test is effective
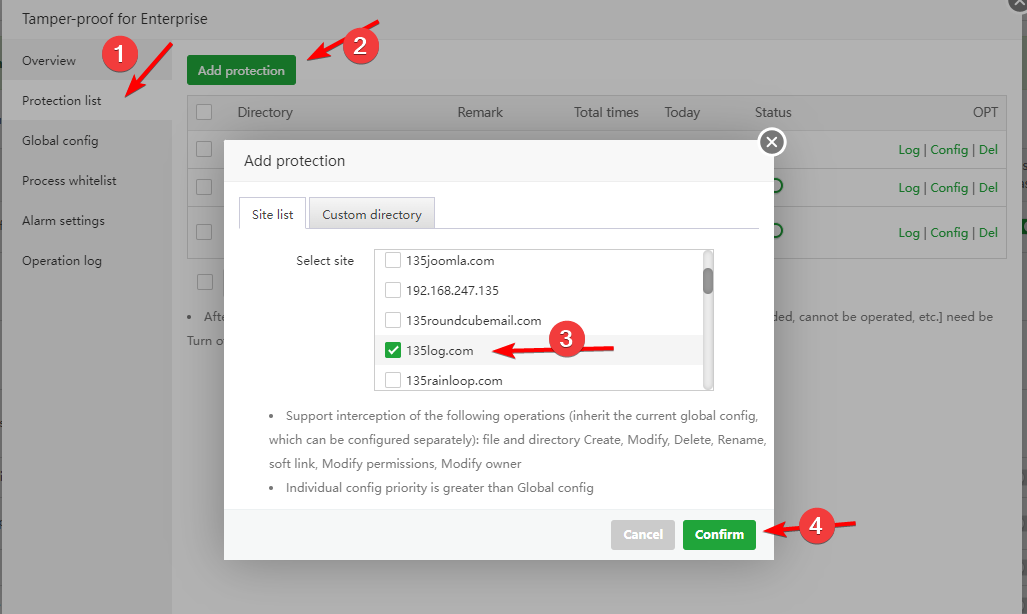
Protection list
- Add a protected site or directory, only valid for this directory, Global config takes precedence
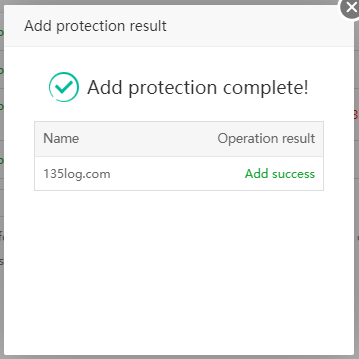
Test and modify the file to check for errors
Prompt save failed
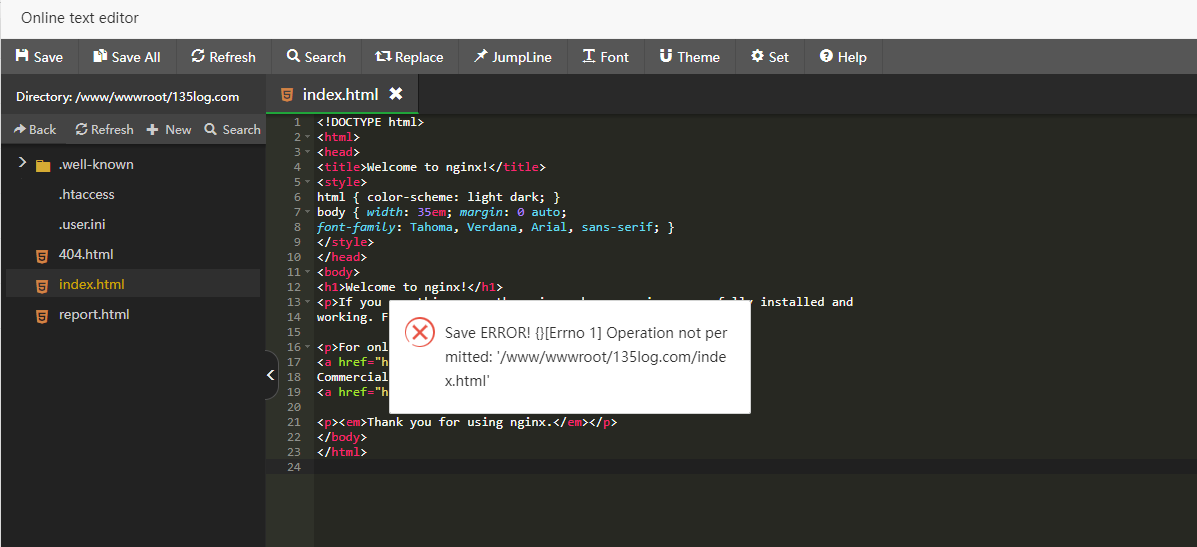
See that /www/wwwroot/135log.com/ has been protected twice
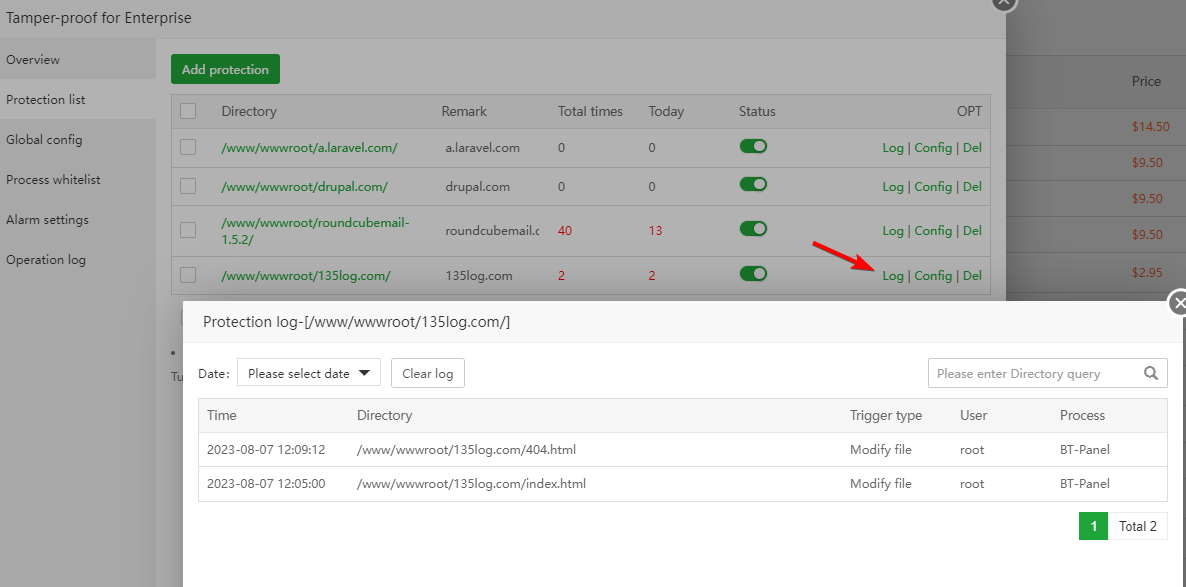
Config
There are Protection switch, Basic Setting, Protected file suffix, Directory whitelist, File whitelist for the protected directory
3.1 Basic Setting
According to these rules, you can configure the anti-tampering in line with your own project
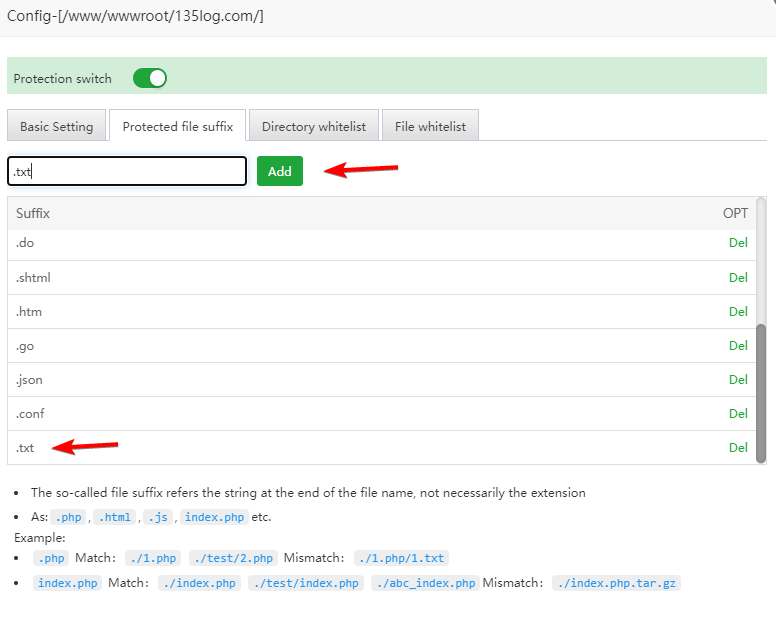
3.2 Protected file suffix
The suffixes are:
.pl
.php
.html
.tpl
.js
.css
.jsp
.do
.shtml
.html
Here the suffix name is understood as a string, look at the end, if the end contains the above suffix name, it can be protected
Such as adding .txt file protection
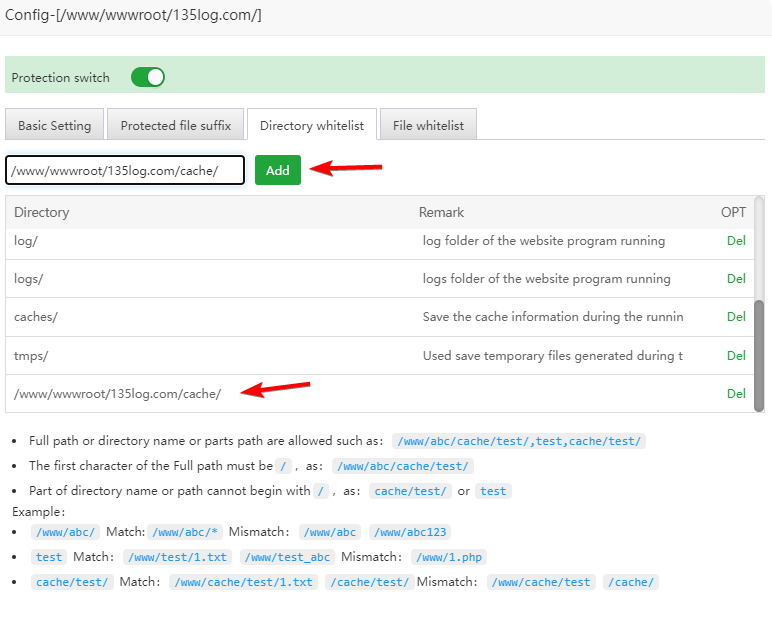
3.3 Directory whitelist
Unprotected file directory name or absolute path can be added
If the cache directory is released, it can be written as /www/wwwroot/135log.com/cache/
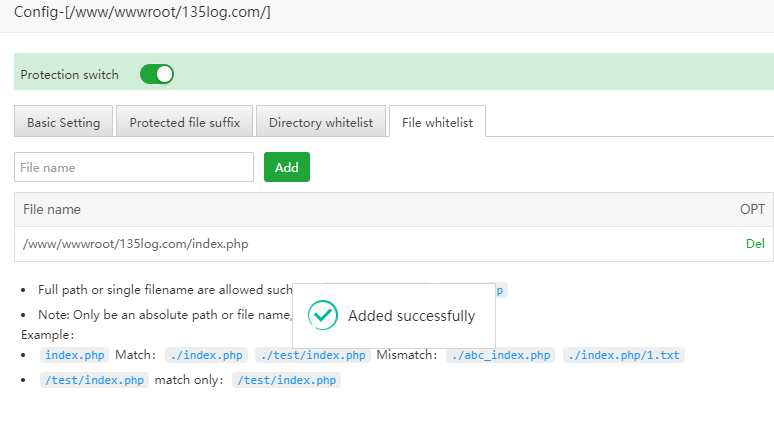
3.4 File whitelist
Exclude unprotected filenames
For example, index.php needs to be released (it is recommended to set an absolute path)
/www/wwwroot/135log.com/index.php
Global config
The rules in the Global config are default and can be modified flexibly according to your actual usage
Basic Setting
According to these rules, you can configure the anti-tampering in line with your own project
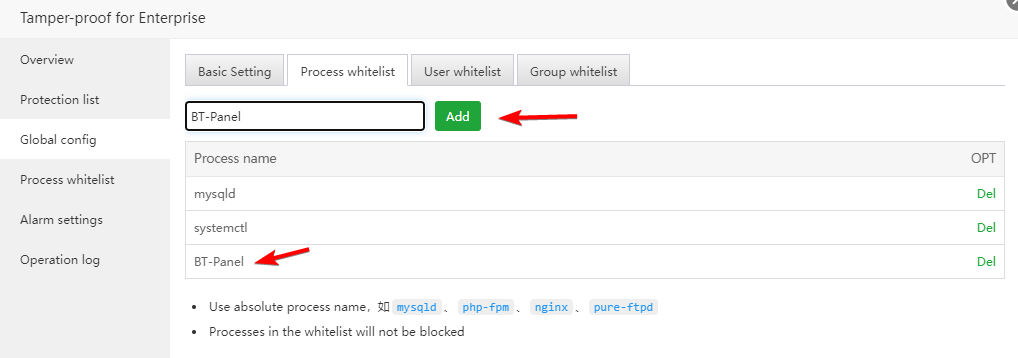
Process whitelist:
When adding, be sure to fill in the absolute process name, such as the process of the panel: BT-Panel
Note: Any operations of this process will not be intercepted after being added.
- Group whitelist、User whitelist:
After it is enabled, any operations of users or user groups will not be blocked.
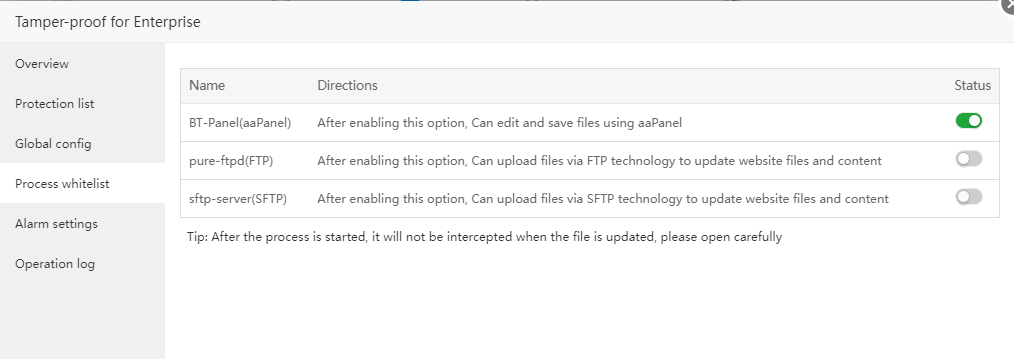
Process whitelist
Consistent with the Process whitelist function of Global config, three commonly used processes are preset
Alarm settings
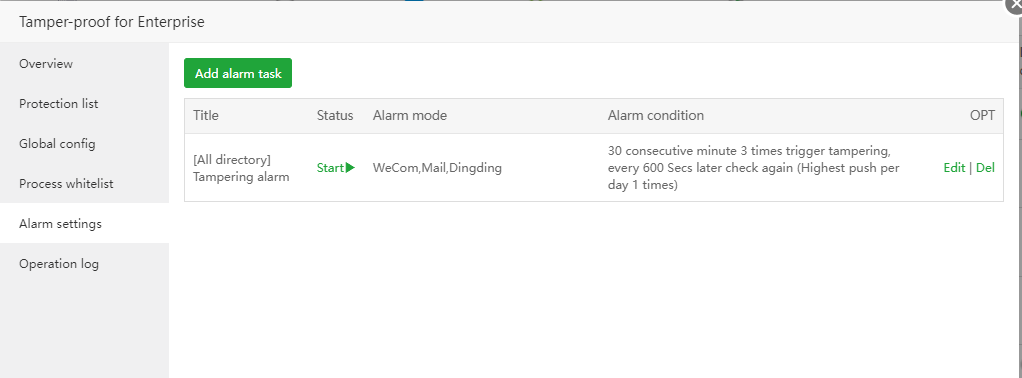
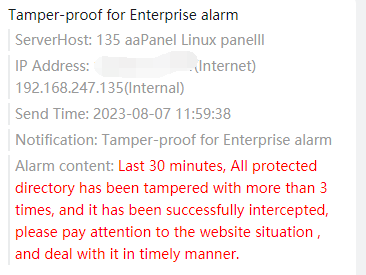
Used to notify Tamper-proof for Enterprise of interception
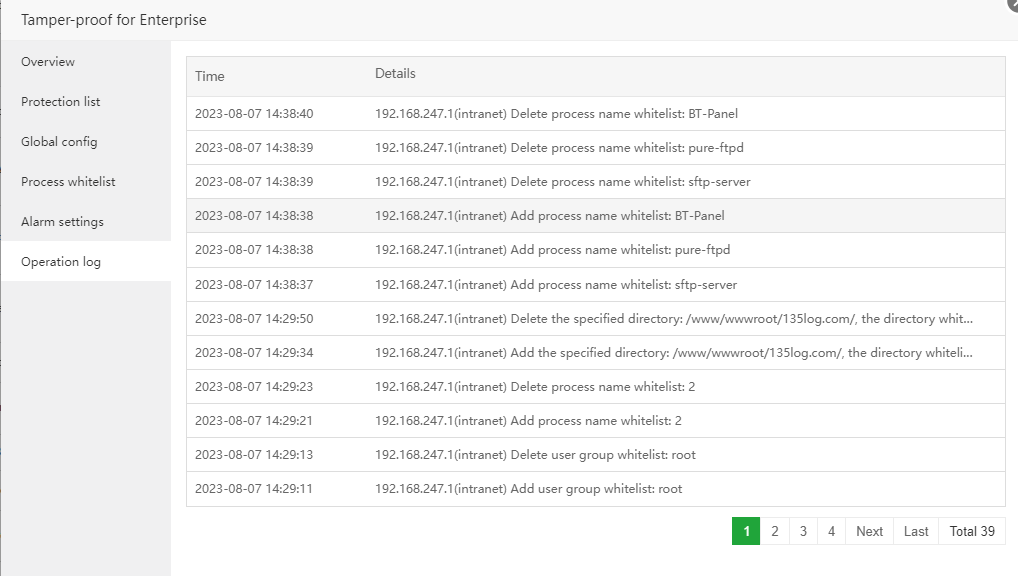
Operation log
See the operations on Tamper-proof for Enterprise, such as adding a whitelist, adding a protection list, switching, and a series of operations
Error:
Cannot start if installed
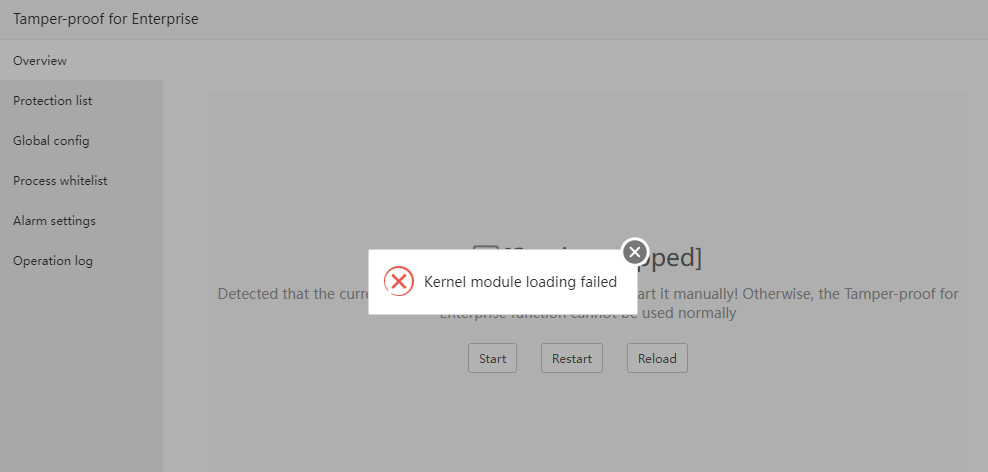
Try the following:
First go to the server provider website to make a server snapshot backup, then use the ssh tool to execute commands to upgrade system dependencies
Centos:
yum update
Debian/ubuntu:
apt update && apt upgrade
After the update is complete, restart the server, wait for the system to restart, open the panel, uninstall the previous Tamper-proof for Enterprise, and reinstall
Currently Tamper-proof for Enterprise is developed based on the kernel, if the kernel version is too low or not within the compatible range, it cannot be used normally