Introduction to Defense CC
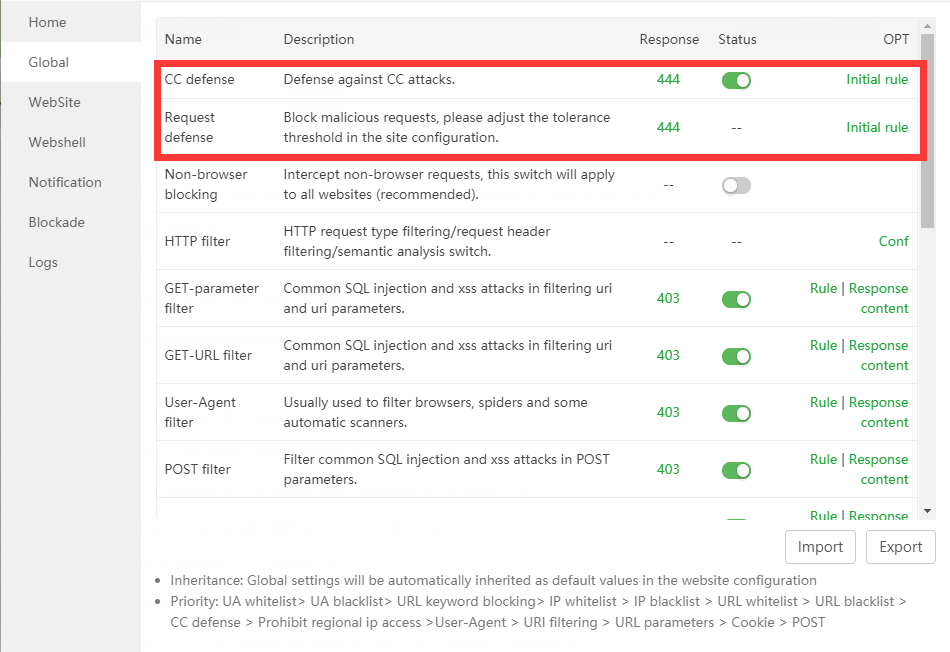
The difference between CC defense and malicious request tolerance
- CC defense refers to the interception of IP when an IP triggers the threshold you set
- Malicious request tolerance refers to the number of malicious requests made by an IP to block the IP
For example:
CC attack
The attacker's IP is 192.168.1.10. This IP accessed the website www.aapanel.com/index.php 666 times within 60 seconds. Then the WAF considers it to be a CC attack and intercepts it
Malicious request tolerance
The attacker's IP is 192.168.1.10. This IP has attacked the website www.aapanel.com 10 times within 60 seconds (malicious behavior), then the firewall considers this to be an illegal IP and intercepts it
CC defense settings
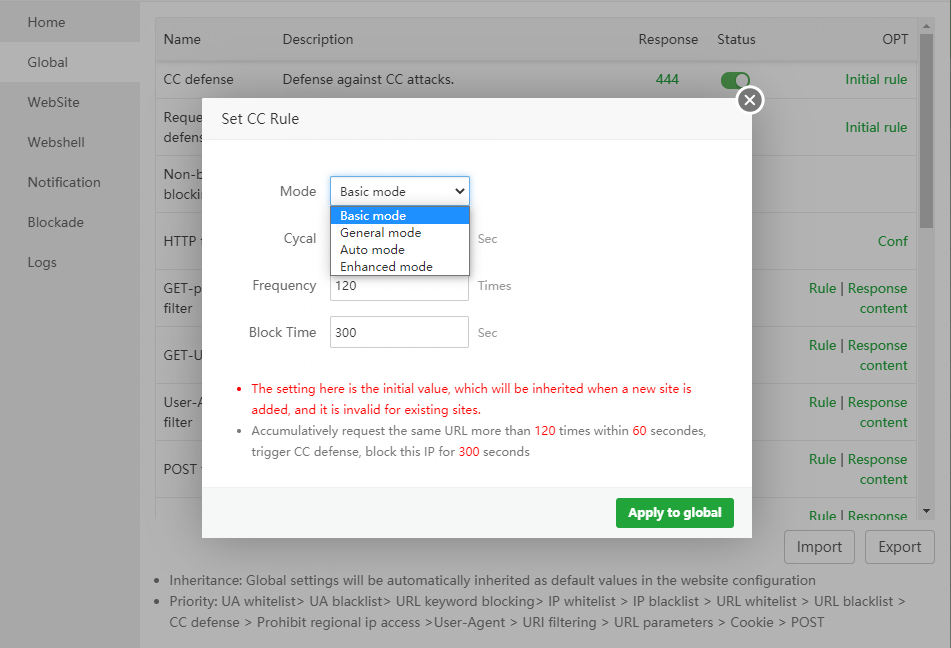
Basic mode
We have a default value for inexperienced users. The default value will try to minimize parameter error interception, if you don't know your own website very well. Or if you don't know much about CC. Can use this mode
General mode
The interception threshold of the general mode is higher than that of the basic mode. If there is no problem in the basic mode, you can not use this mode
Auto mode

Here we need to focus on the internal logic of the automatic mode
1.When the website is accessed 600 times within 60 seconds, the enhanced mode is automatically turned on, and the enhanced mode is automatically turned off if the rule is not triggered.
2.This 600 times represents all requests. Including requests for static files such as JS and pictures. For example, if your website has a PV of 600,000 times a day, you can calculate that your website is accessed 600,000/86400*60=360 times per second on average.
3.Multiplying this number by 10 is almost the threshold you need to set, which is 3600. Why multiply it by 10 because this number includes the number of static files and pictures.
Enhanced mode
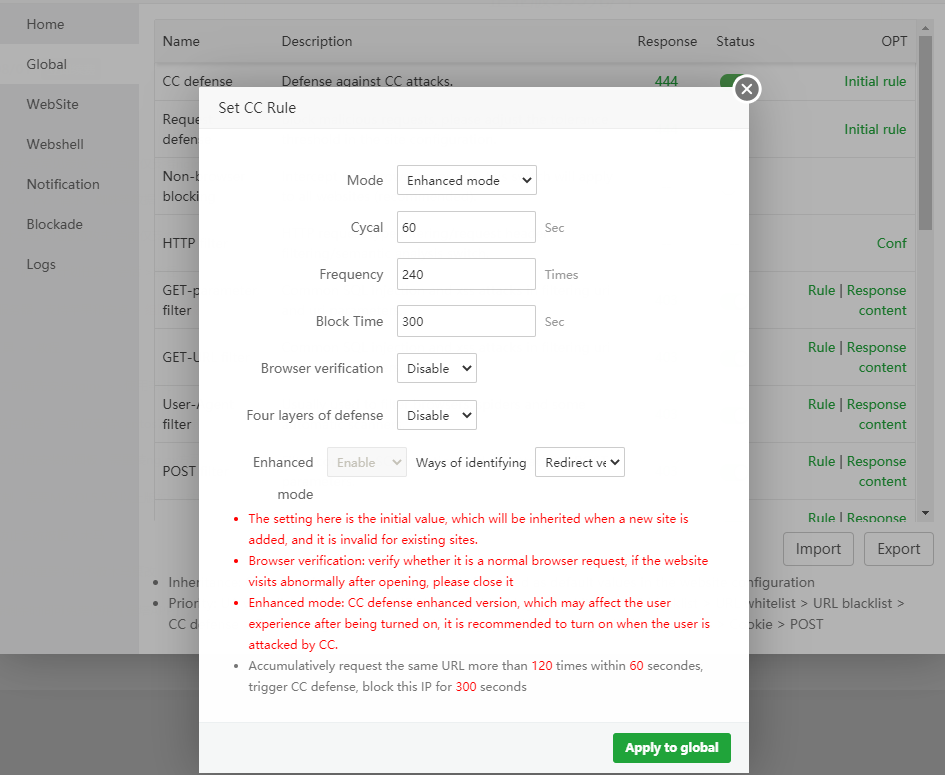
This mode is generally rarely turned on. Unless encountered by a large number of CC attacks, the server resources are exhausted.
There are two options in the enhanced mode, one is JS verification, the other is verification code verification.
If your website is very slow, it may be attacked by a large number of CCs. Then it is recommended to turn on the enhanced mode (recommended to use verification code verification)
Enhanced mode is to force the browser behavior to verify whether the client IP is normal
For example, the effect of turning on the verification code mode is as follows:
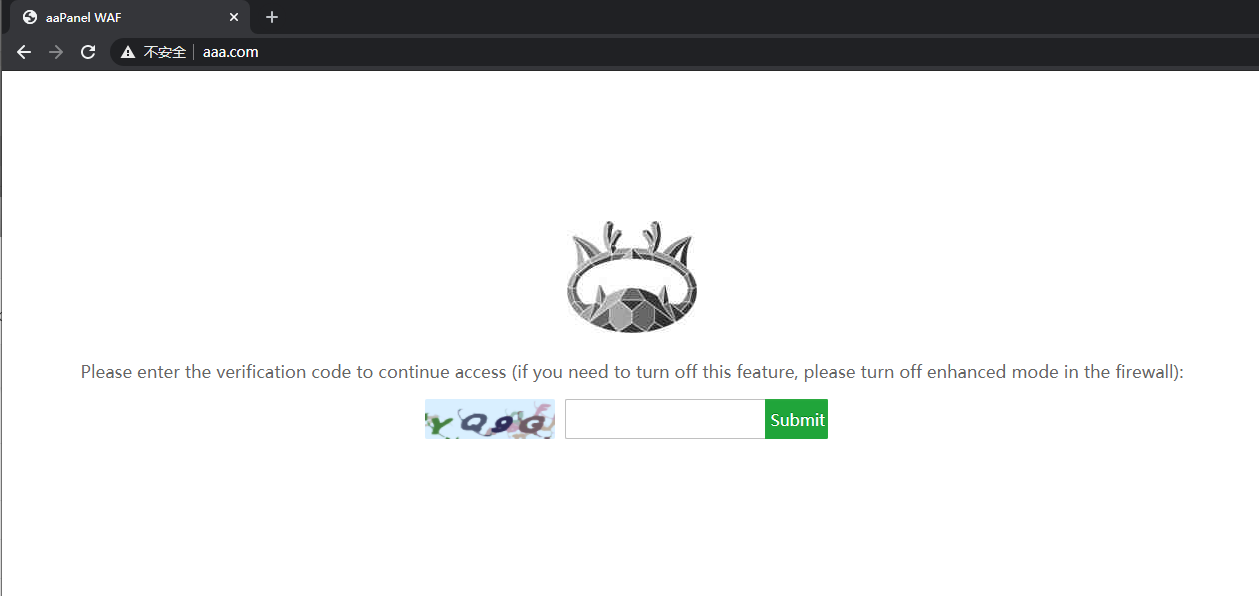
If the verification code cannot be displayed. Then open the url rewrite of your website to see if there is this paragraph. if so. Just delete this paragraph
if (!-e $request_filename) {
return 404;
}
Browser verification
This is also available when the automatic mode or enhanced mode is turned on. This is because there is no need to verify whether the client IP is malicious in the normal mode or the Xiaobai mode.
The advantage of this verification is that it will automatically determine whether the behavior of this IP is a normal browser behavior.
Four layers of defense
This is a function to block IP through the system firewall. When being attacked by a large number of CCs. WAF is a seven-layer application, and the blocked IP can also enter the network card to access the application layer. Although the data cannot be accessed. But it will still cause some memory loss to the server.